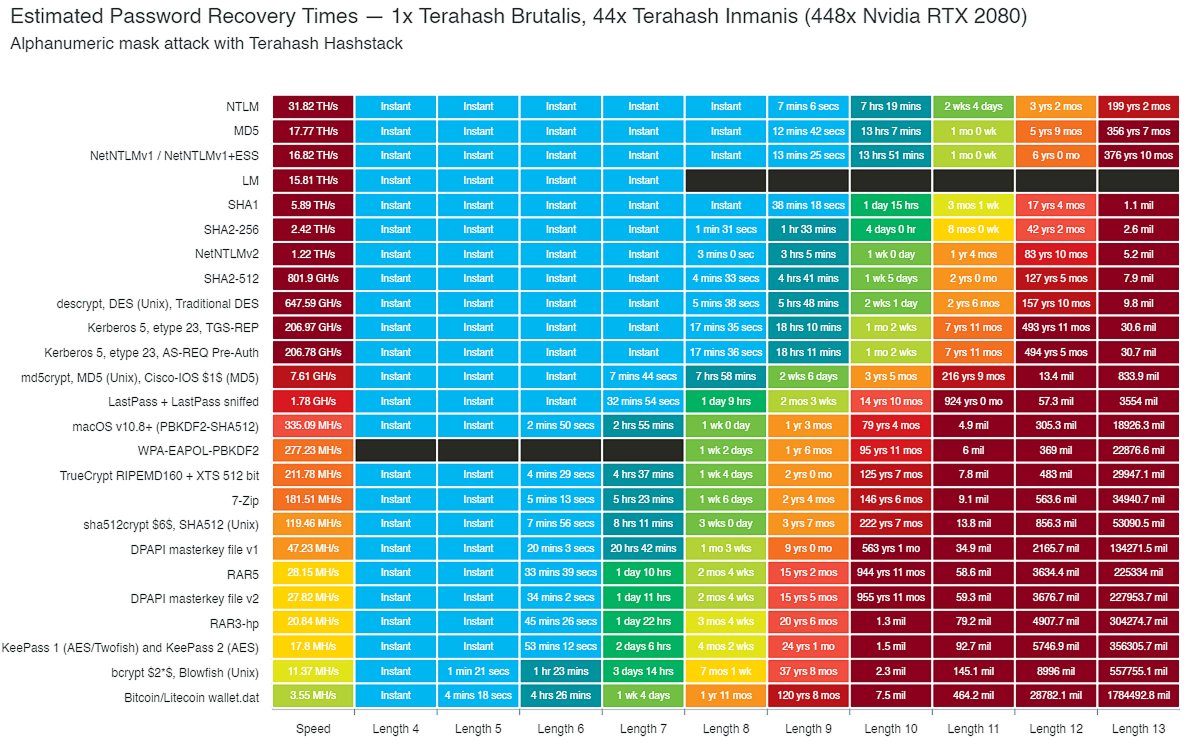
The Walls Are Cracking: New Report Alleges FBI, NSA Demand Passwords, Security Data When Spying On Users | HotHardware
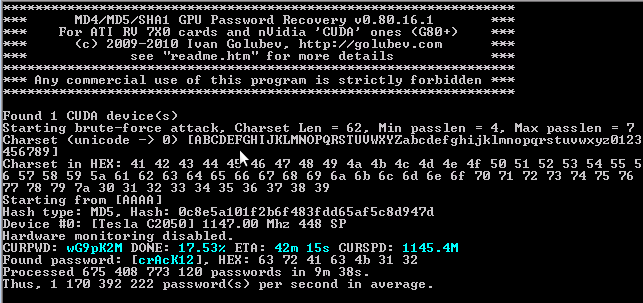
I built an insanely fast Electrum (pre v2.8, 2017) password cracking cluster using FPGAs. Runs at 30 billion tries per second using 2kW of power. At your service! : r/Bitcoin